Ever wondered how devices talk to each other without getting hacked? Well, SSH IoT applications are the unsung heroes behind secure communication in the world of connected devices. Imagine your smart fridge chatting with your grocery app or your security camera syncing with your phone. But how do they do it safely? That’s where SSH comes in, and it’s about to change the game.
In this digital age, the Internet of Things (IoT) is everywhere. From smart homes to industrial automation, IoT devices are transforming the way we live and work. But with great power comes great responsibility. Security is no longer optional—it’s a must. And that’s where SSH IoT applications step in, ensuring your devices stay safe and sound.
So, why should you care? Because without proper security, your IoT setup could become a playground for hackers. But don’t worry, we’ve got you covered. In this article, we’ll dive deep into SSH IoT applications, breaking down how they work, why they matter, and how you can use them to secure your connected world. Let’s get started!
Read also:Bollyflix Site Your Ultimate Destination For Bollywood Entertainment
Table of Contents
- What is SSH?
- SSH IoT Applications: An Overview
- Benefits of Using SSH in IoT
- SSH and IoT Security
- Common SSH IoT Applications
- Implementing SSH in IoT
- Challenges in SSH IoT Applications
- The Future of SSH IoT
- Best Practices for SSH IoT Security
- Conclusion
What is SSH?
SSH, or Secure Shell, is like the bodyguard of the internet. It’s a network protocol that lets you access remote devices securely. Think of it as a secret tunnel that only authorized users can enter. SSH encrypts all the data flowing between devices, making it super hard for hackers to intercept.
But here’s the kicker: SSH isn’t just for computers. It’s also a game-changer for IoT devices. With SSH, you can manage and monitor your gadgets from anywhere in the world, without worrying about prying eyes. And let’s face it, in this age of cyber threats, that’s a pretty big deal.
SSH IoT Applications: An Overview
How SSH Works in IoT
SSH in IoT is all about creating a secure connection between devices. Let’s say you’ve got a smart thermostat at home. With SSH, you can tweak its settings from your phone, even if you’re miles away. The best part? No one else can get in unless they’ve got the keys.
SSH uses something called public-key cryptography. Think of it like a lock and key system. Your device has a public key that’s shared with others, and a private key that stays secret. When you want to connect, the devices exchange keys to make sure they’re legit. It’s like a secret handshake that only trusted buddies can do.
Why SSH Matters in IoT
IoT is awesome, but it’s also a hacker’s dream. With billions of connected devices out there, the attack surface is huge. That’s where SSH comes in. It adds an extra layer of protection, making it harder for bad guys to mess with your gadgets.
Read also:7ster Hdcom Your Ultimate Destination For Highquality Streaming
Plus, SSH isn’t just about security. It also makes device management a breeze. You can update firmware, check logs, and troubleshoot issues—all from the comfort of your couch. And who doesn’t love that?
Benefits of Using SSH in IoT
So, why should you bother with SSH IoT applications? Here are a few reasons:
- Encryption: SSH encrypts all data, keeping it safe from prying eyes.
- Authentication: With public-key cryptography, only authorized users can access your devices.
- Remote Access: Manage your IoT devices from anywhere, as long as you’ve got an internet connection.
- Reliability: SSH is a tried-and-true protocol that’s been around for years, so you know it works.
But wait, there’s more. SSH IoT applications also help you stay compliant with data protection laws. In today’s regulatory landscape, that’s a huge plus.
SSH and IoT Security
Securing IoT Devices with SSH
IoT security is a big deal, and SSH is one of the best tools in your arsenal. By encrypting data and authenticating users, SSH makes it much harder for hackers to break in. But that’s not all. SSH also helps you detect and respond to threats in real-time.
For example, if someone tries to brute-force their way into your device, SSH can lock them out after a few failed attempts. And if they do manage to get in, the encrypted data will be useless to them. It’s like having a digital fortress around your IoT setup.
SSH vs. Other Protocols
Now, you might be wondering, why SSH? Why not use something else, like HTTPS or MQTT? Well, here’s the deal: SSH is specifically designed for secure communication. While other protocols have their strengths, SSH is the gold standard when it comes to security.
For instance, HTTPS is great for web traffic, but it’s not always the best choice for IoT devices. And MQTT, while lightweight and efficient, doesn’t offer the same level of security as SSH. So, if security is your top priority, SSH is the way to go.
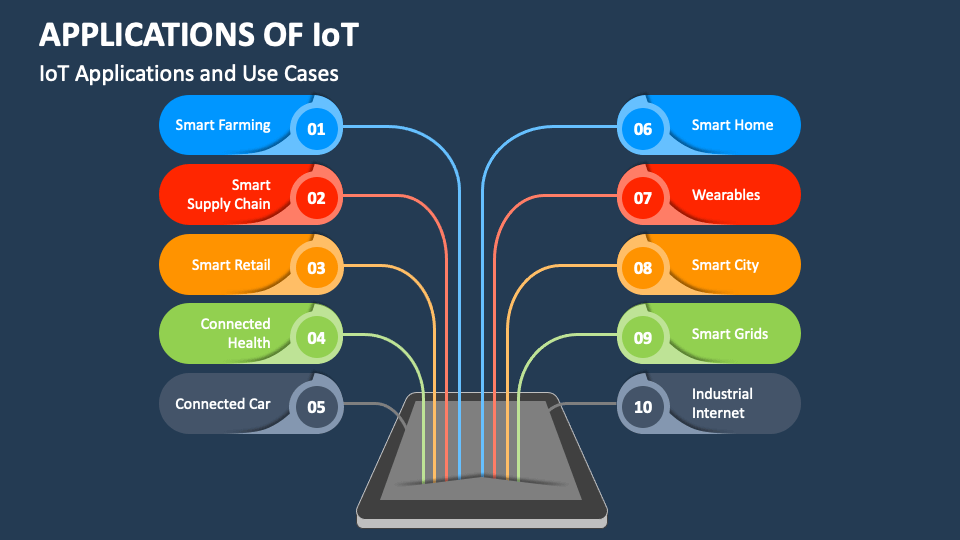
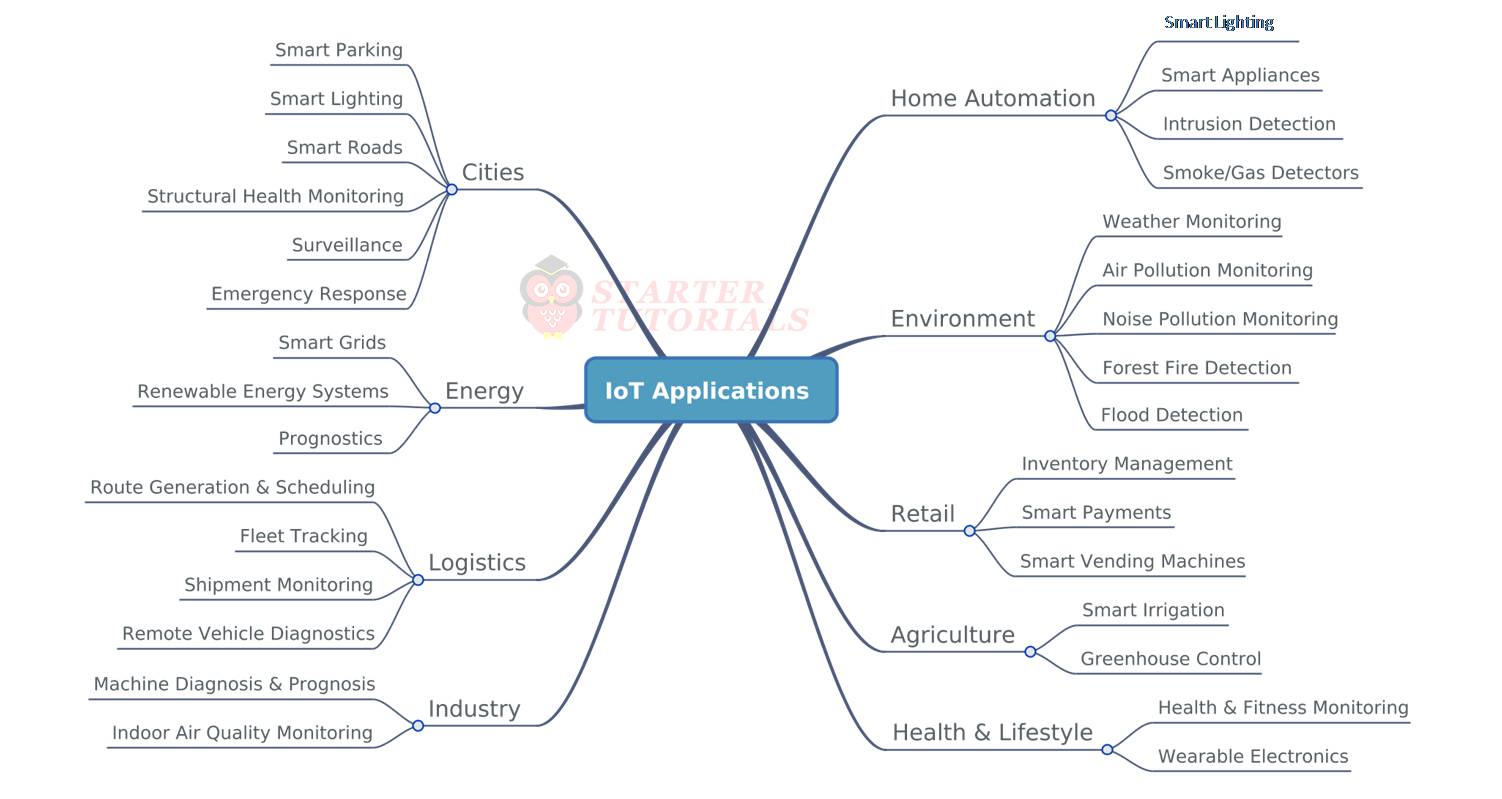
Common SSH IoT Applications
SSH IoT applications are everywhere. Here are a few examples:
- Smart Homes: Use SSH to control your smart lights, thermostats, and security cameras from anywhere.
- Industrial Automation: Securely monitor and manage industrial equipment, even in remote locations.
- Healthcare: Protect sensitive patient data by using SSH to secure medical devices.
- Transportation: Ensure the safety of connected vehicles by using SSH for secure communication.
And that’s just the tip of the iceberg. As IoT continues to grow, the possibilities for SSH IoT applications are endless.
Implementing SSH in IoT
Setting Up SSH on IoT Devices
Implementing SSH on IoT devices isn’t as hard as it sounds. Most modern devices come with SSH pre-installed, so you just need to enable it. Here’s a quick guide:
- Log in to your device’s admin panel.
- Find the SSH settings and enable the service.
- Generate public and private keys for authentication.
- Test the connection to make sure everything’s working.
Of course, the exact steps may vary depending on your device, but the general process is pretty straightforward.
Best Tools for SSH IoT
There are plenty of tools out there to help you implement SSH IoT applications. Some popular ones include:
- OpenSSH: A free and open-source SSH implementation that’s widely used.
- Putty: A popular SSH client for Windows users.
- SSHFS: A file system that lets you access remote files over SSH.
With the right tools, setting up SSH IoT applications can be a breeze.
Challenges in SSH IoT Applications
Of course, nothing’s perfect. While SSH IoT applications offer tons of benefits, they also come with a few challenges:
- Complexity: Setting up SSH can be tricky, especially for beginners.
- Resource Constraints: Some IoT devices have limited processing power, which can make SSH slow.
- Maintenance: Keeping SSH up-to-date and secure requires regular effort.
But don’t let these challenges scare you off. With a little effort, you can overcome them and reap the rewards of SSH IoT applications.
The Future of SSH IoT
As IoT continues to evolve, so will SSH IoT applications. We’re already seeing new innovations, like quantum-resistant cryptography, that will make SSH even more secure. And with the rise of 5G and edge computing, the possibilities for SSH IoT are limitless.
Imagine a world where every device is securely connected, from your toaster to your car. With SSH IoT applications, that world is closer than you think. So, buckle up, because the future of IoT security is here.
Best Practices for SSH IoT Security
To get the most out of SSH IoT applications, follow these best practices:
- Use Strong Keys: Longer keys are harder to crack, so go for at least 2048 bits.
- Disable Password Authentication: Stick to public-key authentication for added security.
- Limit Access: Only allow trusted users to connect to your devices.
- Keep Software Updated: Regularly update your SSH software to fix any vulnerabilities.
By following these tips, you can make sure your SSH IoT applications are as secure as possible.
Conclusion
SSH IoT applications are the key to a secure and connected future. Whether you’re managing a smart home or running an industrial operation, SSH can help you stay safe and in control. So, don’t wait—start exploring SSH IoT applications today and take your IoT setup to the next level.
And remember, security isn’t just a feature—it’s a necessity. By using SSH IoT applications, you’re not just protecting your devices—you’re protecting your peace of mind. So, what are you waiting for? Get out there and secure your IoT world!
Got any questions or comments? Drop them below, and let’s keep the conversation going. And if you found this article helpful, don’t forget to share it with your friends. Together, we can make the IoT world a safer place for everyone.