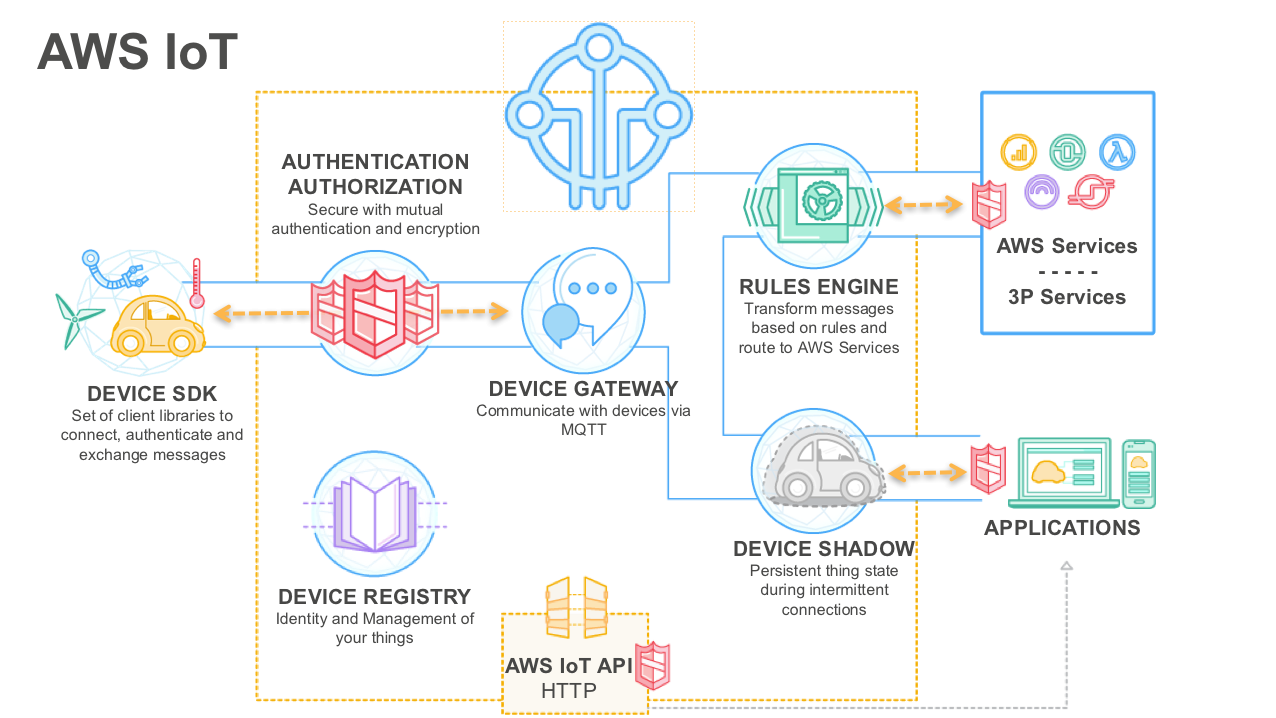
Alright folks, let's talk about something that's getting bigger every day—connecting IoT devices to AWS using SSH. This isn’t just a tech buzzword anymore; it’s a real game-changer for businesses and developers who want to make their devices smarter and more secure. If you're reading this, chances are you're either trying to figure out how SSH works with AWS IoT, or you're already knee-deep in the process but need some clarity. Either way, you're in the right place. Today, we’re breaking it down step by step so it’s super easy to follow.
Now, let me set the stage for you. Imagine you’ve got a bunch of IoT devices—cameras, sensors, smart home gadgets—and you want them all talking to each other through AWS. But here’s the thing: security is key. You don’t want random people accessing your data or controlling your devices, right? That’s where SSH comes in. SSH stands for Secure Shell, and it’s like a digital bodyguard for your device-to-device communication. It’s what we’re going to dive into today.
Before we jump into the nitty-gritty, let’s get one thing straight: this isn’t just about setting up connections. It’s about doing it securely, efficiently, and with the right tools. By the time you finish reading this, you’ll have a solid understanding of how SSH works with AWS IoT, and you’ll be ready to roll up your sleeves and start implementing it yourself. So, buckle up, because we’re about to take you on a ride!
Read also:Kat Timpf New Baby Name The Cutest Addition To The Family
Understanding SSH in AWS IoT
What Exactly is SSH?
First things first, let’s break down what SSH actually is. SSH, or Secure Shell, is like a secret tunnel that lets you connect to remote devices securely. Instead of sending plain text back and forth, which is like shouting your password in a crowded room, SSH encrypts everything. This means only you and the device you’re connecting to can understand what’s being said. And when you’re dealing with IoT devices that might be collecting sensitive data, that’s a big deal.
SSH isn’t just about encryption, though. It also verifies that the device you’re connecting to is who it says it is. This is called authentication, and it’s what keeps hackers from pretending to be your smart fridge or security camera. So, if you’re thinking about setting up SSH for your IoT devices, you’re already thinking smart.
Why Use SSH with AWS IoT?
Now, you might be wondering, why bother with SSH when AWS already has a bunch of security features? Great question. While AWS does offer some built-in security options, SSH adds an extra layer of protection that’s hard to beat. Here’s why:
- Encryption: SSH encrypts all data sent between your device and AWS, so even if someone intercepts it, they can’t read it.
- Authentication: SSH verifies the identity of both the device and the server, so you know you’re talking to the right thing.
- Flexibility: SSH works with a variety of devices and operating systems, so it’s not limited to just one type of setup.
- Control: With SSH, you can control exactly who has access to your devices and what they can do once they’re connected.
So, if you’re looking for a secure way to manage your IoT devices through AWS, SSH is definitely worth considering.
Setting Up SSH for IoT Devices
Choosing the Right AWS Services
Alright, let’s talk about the AWS services you’ll need to set up SSH for your IoT devices. First up, you’ll want to use AWS IoT Core. This is the main service that lets your devices communicate with AWS. Think of it like a digital switchboard that routes messages between your devices and the cloud.
Next, you’ll need to set up an EC2 instance. This is basically a virtual server where your SSH connections will live. You can think of it like a digital meeting room where your devices can chat securely. By combining AWS IoT Core with an EC2 instance, you’ve got everything you need to start setting up SSH connections for your IoT devices.
Read also:Bollyflix Site Your Ultimate Destination For Bollywood Entertainment
Generating SSH Keys
Now, here’s where things get a little technical, but don’t worry—I’ll walk you through it. To set up SSH, you’ll need to generate SSH keys. These are like digital passports that let your devices prove who they are. Here’s how you do it:
- Open up your terminal or command prompt.
- Type in
ssh-keygenand hit enter. This will generate a new SSH key pair. - You’ll be asked where to save the key. Just hit enter to save it in the default location.
- Next, you’ll be asked for a passphrase. This is like a password for your key, so make it something strong and memorable.
- Once that’s done, you’ll have two files:
id_rsa(your private key) andid_rsa.pub(your public key).
Now, here’s the important part: never share your private key with anyone. It’s like the key to your house—keep it safe!
Configuring Your IoT Devices
Once you’ve got your SSH keys, it’s time to configure your IoT devices. This part can vary depending on the type of device you’re using, but the general steps are pretty straightforward:
- Install an SSH client on your device. Most Linux-based devices already have one built in, but you might need to install one on Windows or macOS devices.
- Add your public key to the device’s authorized keys file. This lets the device know it’s okay to accept connections from you.
- Set up a firewall rule to allow SSH traffic. This is usually done through the AWS Security Group settings.
Once you’ve done all that, your device should be ready to accept SSH connections. Pretty cool, right?
Best Practices for Secure Connections
Using Strong Passwords and Passphrases
Alright, let’s talk about something super important: passwords. I know it’s tempting to use something simple like "password123," but trust me, that’s a recipe for disaster. Instead, use strong, unique passwords for everything related to your SSH setup. Here’s what makes a good password:
- At least 12 characters long
- A mix of uppercase and lowercase letters, numbers, and symbols
- Something that’s not easy to guess, like "password" or "123456"
And don’t forget about your SSH key passphrase! This is just as important as your password, so make it strong and keep it safe.
Regularly Updating Your Devices
Another key part of keeping your SSH connections secure is keeping your devices up to date. This means installing the latest software updates and security patches as soon as they’re available. Why? Because hackers are always looking for vulnerabilities, and outdated software is like leaving the door unlocked for them.
Most devices will let you set up automatic updates, so you don’t even have to think about it. Just make sure you’re checking in regularly to make sure everything’s running smoothly.
Monitoring Your Connections
Finally, don’t forget to keep an eye on your SSH connections. This means checking logs regularly to see who’s connecting to your devices and what they’re doing. If you notice anything suspicious, like a connection from an unfamiliar IP address, it’s time to investigate.
Most SSH clients will let you set up alerts for unusual activity, so you can stay on top of things without having to constantly check everything manually. It’s like having a security guard watching your devices 24/7.
Common Challenges and Solutions
Connection Issues
Let’s face it: sometimes things don’t go as planned. If you’re having trouble connecting to your IoT devices via SSH, here are a few things to check:
- Make sure your SSH keys are correctly set up on both your device and your EC2 instance.
- Double-check your firewall rules to ensure SSH traffic is allowed.
- Verify that your device’s SSH service is running and listening on the correct port (usually port 22).
If none of that works, try restarting your device and your EC2 instance. Sometimes a simple reboot can fix a lot of problems.
Security Threats
Security threats are a real concern when it comes to SSH connections. Here are a few common ones to watch out for:
- Brute force attacks: These are when hackers try to guess your password by trying thousands of combinations. To prevent this, use strong passwords and consider setting up two-factor authentication.
- Man-in-the-middle attacks: This is when someone intercepts your SSH connection and tries to steal your data. To protect against this, always use encryption and verify the identity of the devices you’re connecting to.
- Malware: Sometimes devices can get infected with malware that tries to steal your SSH credentials. To prevent this, keep your devices up to date and use antivirus software if available.
By staying vigilant and following best practices, you can keep your SSH connections secure and your data safe.
Future Trends in IoT and SSH
Emerging Technologies
So, where is all this heading? Well, the world of IoT and SSH is evolving quickly, and there are some exciting new technologies on the horizon. For example, quantum computing could change the way we think about encryption and security. While it’s still in its early stages, it has the potential to make SSH connections even more secure in the future.
Another trend to watch is the rise of edge computing. This is where devices process data locally instead of sending it all to the cloud. By combining edge computing with SSH, you can create ultra-secure connections that are faster and more efficient than ever before.
Best Practices for the Future
As technology continues to evolve, it’s important to stay ahead of the curve when it comes to best practices. Here are a few things to keep in mind:
- Stay informed about new security threats and how to protect against them.
- Regularly review and update your security policies to ensure they’re still effective.
- Invest in new technologies that can enhance your SSH connections, like quantum encryption or edge computing.
By staying proactive and embracing new technologies, you can ensure that your SSH connections remain secure and efficient for years to come.
Conclusion
Alright folks, that’s a wrap on our deep dive into SSH connect IoT device AWS. We’ve covered everything from the basics of SSH to setting up secure connections and best practices for keeping your devices safe. Whether you’re a seasoned developer or just starting out, I hope this guide has given you the tools and knowledge you need to take your IoT projects to the next level.
So, what’s next? If you’ve found this article helpful, why not share it with your friends and colleagues? And if you’ve got any questions or comments, feel free to drop them below. Who knows? Your question might just inspire the next big idea!
Table of Contents
- Understanding SSH in AWS IoT
- Setting Up SSH for IoT Devices
- Best Practices for Secure Connections
- Common Challenges and Solutions
- Future Trends in IoT and SSH
- Conclusion