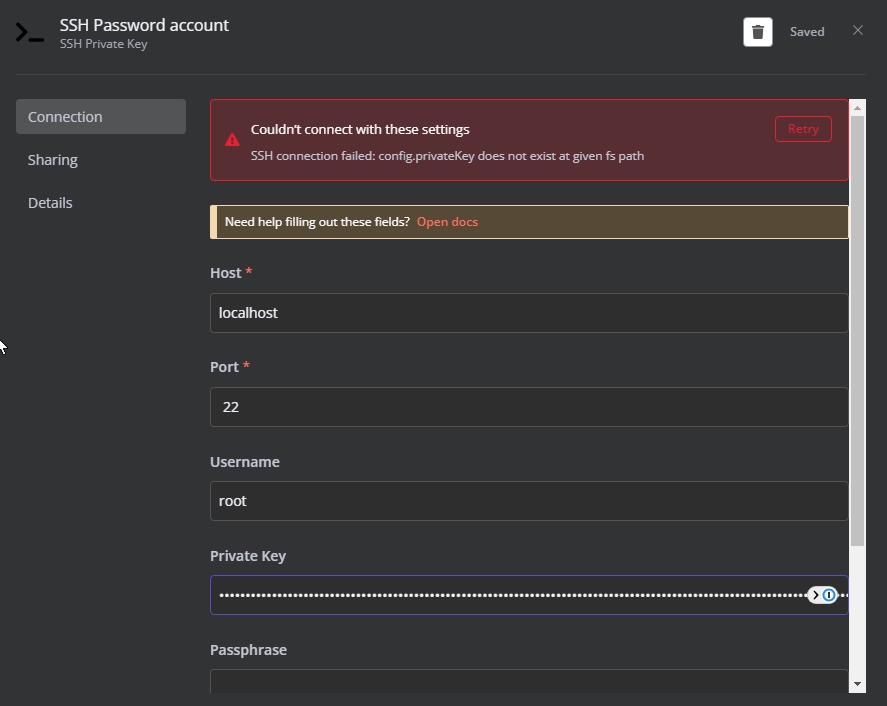
Ever faced the frustrating issue where your RemoteIoT platform SSH key just isn’t working? You’re not alone. Many users encounter this problem, and it can halt your entire workflow. Whether you're a seasoned developer or a beginner, understanding why your SSH key fails and how to fix it is crucial for seamless remote access.
Let’s face it, SSH keys are like the VIP passes to your server. They allow you to securely connect without passwords, saving you time and enhancing security. But what happens when this access is denied? That’s where we come in. This article will walk you through everything you need to know about troubleshooting and resolving SSH key issues on the RemoteIoT platform.
From basic setup tips to advanced debugging techniques, we’ve got you covered. So grab your coffee, sit back, and let’s dive deep into the world of SSH keys and RemoteIoT troubleshooting. Ready? Let’s go!
Read also:Cheri Oteri Partner The Untold Story Behind The Comedy Queens Love Life
Understanding SSH Keys in RemoteIoT Platform
Before we jump into the nitty-gritty of troubleshooting, let’s take a moment to understand what SSH keys are and why they matter in the RemoteIoT platform. SSH keys are cryptographic keys that provide secure authentication between your local machine and the remote server. In simpler terms, they act as a lock and key system, ensuring only authorized users can access the server.
When you set up an SSH key on the RemoteIoT platform, you’re essentially creating a secure tunnel for communication. This eliminates the need for password authentication, which can be prone to brute-force attacks. However, when the SSH key stops working, it can disrupt your workflow and lead to significant downtime.
Here’s a quick rundown of why SSH keys are important:
- Security: SSH keys provide stronger security compared to traditional passwords.
- Convenience: Once set up, you don’t need to enter a password every time you connect to the server.
- Efficiency: Automating tasks with SSH keys can save you a ton of time.
Common Reasons Why SSH Keys Stop Working
Now that we’ve covered the basics, let’s explore the common reasons why SSH keys might stop working on the RemoteIoT platform. Understanding these issues is the first step toward resolving them. Here are some of the most frequent culprits:
- Incorrect Permissions: The permissions on your SSH key files might be set incorrectly, leading to access issues.
- Key Mismatch: The public key on the server might not match the private key on your local machine.
- Corrupted Keys: Sometimes, the keys themselves can become corrupted, especially if they’ve been edited manually.
- Firewall or Network Issues: Firewalls or network configurations might block SSH connections.
These issues can be frustrating, but don’t worry—we’ll walk you through each one and provide solutions in the following sections.
Step-by-Step Guide to Troubleshooting SSH Key Issues
Troubleshooting SSH key issues can seem daunting, but with the right approach, it’s entirely manageable. Below, we’ll break down the process into simple, actionable steps. Follow along, and you’ll have your SSH key up and running in no time.
Read also:Bollyflix Site Your Ultimate Destination For Bollywood Entertainment
1. Verify Your SSH Key Files
The first step in troubleshooting is to ensure that your SSH key files are intact and correctly configured. Here’s how you can do that:
- Check the location of your SSH keys. Typically, they’re stored in the
~/.sshdirectory. - Ensure that the private key file (e.g.,
id_rsa) has the correct permissions. It should be readable only by the owner. - Verify that the public key file (e.g.,
id_rsa.pub) is correctly uploaded to the RemoteIoT platform.
Pro tip: Always double-check the file permissions using the chmod command. For example, run chmod 600 ~/.ssh/id_rsa to set the correct permissions.
2. Test the SSH Connection
Once you’ve verified your SSH key files, it’s time to test the connection. This step will help you identify if the issue lies with the key itself or something else. Here’s how you can do it:
- Open your terminal and run the command
ssh -v user@remote-server. - Pay attention to the output. It will provide valuable information about the connection process and any errors encountered.
- If the connection fails, look for specific error messages that can guide you toward the solution.
Remember, the -v flag stands for verbose, and it provides detailed output that can help in debugging.
Advanced Debugging Techniques
For more complex issues, advanced debugging techniques can be invaluable. These methods require a deeper understanding of SSH and server configurations, but they can uncover hidden problems. Let’s explore some of these techniques:
1. Check Server Logs
Server logs are a treasure trove of information when it comes to debugging SSH issues. By examining these logs, you can pinpoint the exact cause of the problem. Here’s how:
- Access the server logs using the
journalctlordmesgcommand, depending on your server setup. - Look for entries related to SSH connections and note any error messages.
- Use the information from the logs to address the issue.
Server logs can be overwhelming at first, but with practice, you’ll become proficient in interpreting them.
2. Validate SSH Configuration
Another crucial step is to validate the SSH configuration on both your local machine and the server. Misconfigurations can lead to SSH key failures. Here’s what you need to do:
- Check the
sshd_configfile on the server to ensure that SSH key authentication is enabled. - Look for any restrictions or rules that might block your SSH key.
- Restart the SSH service after making changes to apply them.
Always back up your configuration files before making changes to avoid accidental data loss.
Best Practices for Managing SSH Keys
Prevention is better than cure, and this holds true for SSH key management as well. By following best practices, you can minimize the chances of encountering issues. Here are some tips:
- Use Strong Keys: Generate SSH keys with sufficient bit length (e.g., 4096 bits) for enhanced security.
- Regularly Rotate Keys: Replace old keys periodically to reduce the risk of unauthorized access.
- Limit Access: Restrict SSH key usage to specific users and IP addresses.
Implementing these practices will not only improve security but also make troubleshooting easier in the long run.
Common Mistakes to Avoid
Even the best of us make mistakes, and when it comes to SSH keys, these errors can lead to significant problems. Here are some common mistakes to avoid:
- Hardcoding Keys: Never hardcode SSH keys in scripts or configuration files. This can lead to accidental exposure.
- Using Weak Passwords: If you must use passwords for SSH, ensure they’re strong and unique.
- Ignoring Updates: Keep your SSH client and server software up to date to protect against vulnerabilities.
By steering clear of these pitfalls, you’ll maintain a more secure and reliable SSH setup.
Case Study: Resolving SSH Key Issues on RemoteIoT Platform
To provide a real-world example, let’s look at a case where an SSH key stopped working on the RemoteIoT platform. The user reported being unable to connect to their server despite having a valid SSH key. Here’s how the issue was resolved:
After initial troubleshooting, it was discovered that the user had accidentally changed the permissions of their SSH key files. By resetting the permissions using the chmod command, the connection was restored. Additionally, the user was advised to implement regular key rotation to prevent similar issues in the future.
Key Takeaways from the Case Study
This case highlights the importance of:
- Maintaining correct file permissions.
- Regularly reviewing and updating SSH keys.
- Documenting changes to avoid accidental misconfigurations.
Learning from real-world scenarios can significantly enhance your troubleshooting skills.
Conclusion and Next Steps
In this comprehensive guide, we’ve covered everything you need to know about SSH key issues on the RemoteIoT platform. From understanding the basics of SSH keys to advanced debugging techniques, you’re now equipped to tackle any challenge that comes your way.
Here’s a quick recap of the key points:
- SSH keys are essential for secure and efficient remote access.
- Common issues include incorrect permissions, key mismatches, and network problems.
- Advanced debugging techniques, such as checking server logs, can uncover hidden issues.
- Best practices, like using strong keys and limiting access, enhance security and reliability.
Now it’s your turn to take action. If you’ve encountered SSH key issues, try applying the solutions discussed in this article. And don’t forget to share your experiences in the comments below. Your feedback helps us improve and assists other readers in their troubleshooting journey.
Stay secure, stay connected, and keep troubleshooting!
Table of Contents
- Understanding SSH Keys in RemoteIoT Platform
- Step-by-Step Guide to Troubleshooting SSH Key Issues
- Advanced Debugging Techniques
- Best Practices for Managing SSH Keys
- Common Mistakes to Avoid
- Case Study: Resolving SSH Key Issues on RemoteIoT Platform
Subheadings
- Common Reasons Why SSH Keys Stop Working
- Verify Your SSH Key Files
- Test the SSH Connection
- Check Server Logs
- Validate SSH Configuration
- Key Takeaways from the Case Study