Hey there, tech enthusiasts! If you’ve ever wondered how to secure your IoT devices through AWS with a RemoteIoT VPC SSH setup, you’re in the right place. The world of cloud computing is evolving faster than ever, and AWS continues to lead the pack with its powerful tools. But let’s be real, navigating the complexities of RemoteIoT VPC SSH AWS can feel like trying to solve a Rubik’s Cube blindfolded. Don’t worry, though—we’ve got your back!
Picture this: you’ve got a fleet of IoT devices spread across the globe, all connected to AWS. You want to ensure that your data is secure, your network is protected, and your SSH connections are rock-solid. Sounds overwhelming, right? Well, it doesn’t have to be. In this guide, we’ll break down everything you need to know about RemoteIoT VPC SSH AWS, from setting up your VPC to securing your SSH connections.
Whether you’re a seasoned developer or just starting out in the world of cloud computing, this article will give you the tools and knowledge to take control of your IoT infrastructure. So, buckle up, grab a coffee, and let’s dive into the nitty-gritty of RemoteIoT VPC SSH AWS!
Read also:Ariana Grandes Daughter How Old Is She And Everything You Need To Know
Understanding RemoteIoT VPC SSH AWS
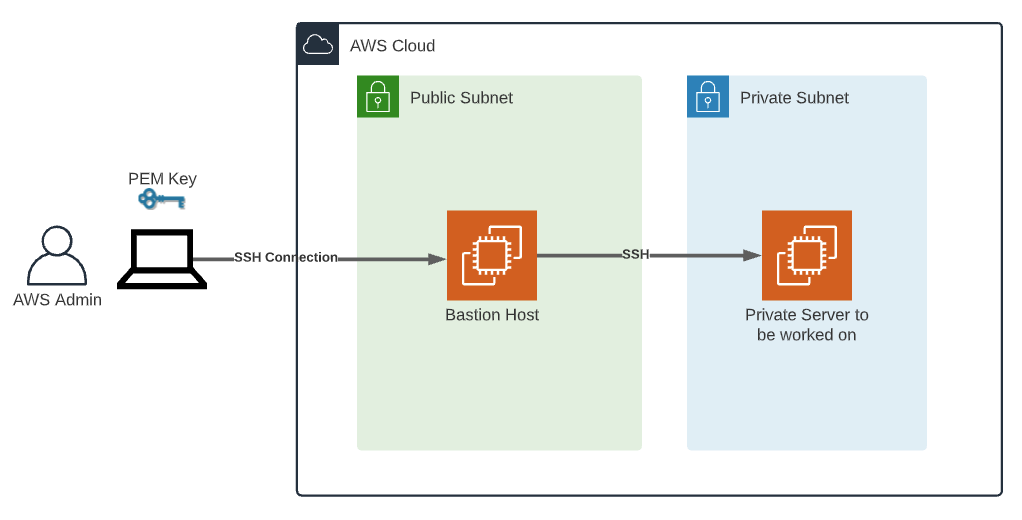
Before we get into the juicy details, let’s talk about what RemoteIoT VPC SSH AWS actually means. At its core, it’s all about creating a secure environment for your IoT devices using AWS’s Virtual Private Cloud (VPC) and SSH (Secure Shell). Think of it as building a fortress around your data, where only authorized users can enter.
Here’s a quick breakdown:
- RemoteIoT: Refers to IoT devices that operate remotely, often in different geographical locations.
- VPC: A Virtual Private Cloud is essentially a private network within AWS where you can launch your resources.
- SSH: Secure Shell is a protocol used to securely access remote servers or devices.
- AWS: Amazon Web Services is the cloud platform that powers it all.
By combining these elements, you can create a secure and scalable infrastructure for your IoT devices. But why stop at understanding the basics? Let’s explore how you can implement this in your own projects.
Setting Up Your VPC for RemoteIoT
Setting up a VPC is like laying the foundation for a house. If you don’t get it right, everything else will crumble. Here’s how you can set up your VPC for RemoteIoT:
Step 1: Create a New VPC
Head over to the AWS Management Console and navigate to the VPC dashboard. Click on "Create VPC" and configure the settings according to your needs. Make sure to choose a CIDR block that suits the size of your network.
Read also:Andres Muhlach Height In Feet Everything You Need To Know About This Rising Star
Step 2: Configure Subnets
Subnets are like rooms in your house. You’ll want to create public and private subnets to ensure that your IoT devices are properly segregated. Public subnets can be accessed from the internet, while private subnets remain hidden.
Step 3: Set Up Security Groups
Security groups act as virtual firewalls for your instances. Define rules that allow or deny traffic based on IP addresses, ports, and protocols. For SSH, you’ll want to allow traffic on port 22, but only from trusted IP addresses.
Best Practices for VPC Configuration
When configuring your VPC, keep these best practices in mind:
- Use separate VPCs for different environments (e.g., development, testing, production).
- Enable VPC Flow Logs to monitor traffic and detect potential security threats.
- Regularly review and update your security groups to reflect changes in your network.
Securing Your SSH Connections
Now that your VPC is set up, it’s time to focus on securing your SSH connections. SSH is a powerful tool, but if not configured correctly, it can leave your network vulnerable to attacks. Here’s how you can lock it down:
Step 1: Use Key-Based Authentication
Passwords are so 2000-and-late. Use SSH keys instead. They’re more secure and eliminate the risk of brute-force attacks. Generate a key pair using tools like SSH-Keygen and store your private key in a secure location.
Step 2: Disable Root Login
Root access is like handing the keys to your house to a stranger. Disable it and use a regular user account with sudo privileges instead. This adds an extra layer of security to your system.
Step 3: Change the Default SSH Port
Attackers often target the default SSH port (22). Change it to something less obvious, like 2222 or 443. Just make sure to update your security group rules accordingly.
Advanced SSH Security Tips
For an extra dose of security, consider these advanced tips:
- Implement two-factor authentication (2FA) for SSH connections.
- Use fail2ban to automatically block IP addresses that attempt too many failed login attempts.
- Regularly update your SSH server software to patch any vulnerabilities.
Integrating IoT Devices with AWS
Once your VPC and SSH are set up, it’s time to integrate your IoT devices with AWS. This is where the magic happens. AWS offers several services that make it easy to manage your IoT devices, including:
- AWS IoT Core: A managed cloud service that lets you securely connect IoT devices to AWS.
- AWS IoT Device Management: Helps you monitor, organize, and manage your IoT devices at scale.
- AWS IoT Analytics: Provides advanced analytics capabilities to extract insights from your IoT data.
By leveraging these services, you can create a fully integrated and secure IoT ecosystem within AWS.
Best Practices for IoT Integration
When integrating IoT devices with AWS, follow these best practices:
- Use MQTT for lightweight and efficient communication between devices.
- Encrypt all data in transit and at rest using strong encryption protocols.
- Regularly update your device firmware to patch any security vulnerabilities.
Monitoring and Managing Your RemoteIoT VPC SSH AWS
Setting up your infrastructure is just the beginning. To ensure everything runs smoothly, you’ll need to monitor and manage your RemoteIoT VPC SSH AWS setup. Here’s how:
Step 1: Use AWS CloudWatch
CloudWatch is your go-to tool for monitoring AWS resources. Set up alarms to notify you of any unusual activity, such as unexpected SSH login attempts or high CPU usage.
Step 2: Implement AWS Config
AWS Config helps you assess, audit, and evaluate the configurations of your AWS resources. Use it to ensure compliance with security best practices and detect any misconfigurations.
Step 3: Automate with AWS Lambda
Automate repetitive tasks using AWS Lambda functions. For example, you can create a Lambda function that automatically updates your security groups based on changes in your network.
Tools for Managing IoT Devices
Here are some tools that can help you manage your IoT devices:
- AWS IoT Device Defender: Detects and alerts you to security vulnerabilities in your IoT devices.
- AWS Systems Manager: Helps you manage your AWS resources and troubleshoot issues.
- AWS Trusted Advisor: Provides personalized recommendations to optimize your AWS usage.
Scaling Your RemoteIoT VPC SSH AWS Setup
As your IoT infrastructure grows, you’ll need to scale your RemoteIoT VPC SSH AWS setup to meet increasing demands. Here are some tips for scaling:
Step 1: Use Auto Scaling
Auto Scaling automatically adjusts the number of instances based on demand. This ensures that your infrastructure can handle spikes in traffic without compromising performance.
Step 2: Implement Load Balancing
AWS Elastic Load Balancer distributes incoming traffic across multiple instances, improving availability and reliability. Use it to ensure that your IoT devices are always accessible.
Step 3: Optimize Costs
Scaling doesn’t have to break the bank. Use AWS Cost Explorer to analyze your spending and identify areas for optimization. Consider using Spot Instances for non-critical workloads to save costs.
Strategies for Cost Optimization
Here are some strategies for optimizing costs:
- Use Reserved Instances for predictable workloads.
- Right-size your instances to match your actual needs.
- Terminate unused resources to avoid unnecessary charges.
Common Challenges and Solutions
Like any technology, RemoteIoT VPC SSH AWS comes with its own set of challenges. Here are some common issues and how to solve them:
- Challenge: SSH Connection Issues – Solution: Check your security group rules and ensure that the correct ports are open.
- Challenge: High Latency – Solution: Use AWS Global Accelerator to improve performance across regions.
- Challenge: Data Security Breaches – Solution: Regularly audit your security settings and patch any vulnerabilities.
Staying Ahead of the Curve
Technology is constantly evolving, and so should your approach to RemoteIoT VPC SSH AWS. Stay updated with the latest trends and best practices by following AWS blogs, attending webinars, and participating in online communities.
Conclusion: Taking Control of Your IoT Infrastructure
And there you have it—your ultimate guide to mastering RemoteIoT VPC SSH AWS. By following the steps outlined in this article, you can create a secure, scalable, and efficient IoT infrastructure that meets the demands of today’s digital world.
Remember, security should always be your top priority. Use strong authentication methods, keep your systems updated, and regularly monitor your network for any suspicious activity. And don’t forget to leverage AWS’s powerful tools to manage and optimize your IoT devices.
So, what are you waiting for? Take action now! Share this article with your friends, leave a comment below, and let us know how you’re using AWS to power your IoT projects. Together, we can build a safer and more connected world!
References
For further reading, check out these trusted sources:
Table of Contents
- Understanding RemoteIoT VPC SSH AWS
- Setting Up Your VPC for RemoteIoT
- Securing Your SSH Connections
- Integrating IoT Devices with AWS
- Monitoring and Managing Your RemoteIoT VPC SSH AWS
- Scaling Your RemoteIoT VPC SSH AWS Setup
- Common Challenges and Solutions
- Conclusion: Taking Control of Your IoT Infrastructure
- References