Hey there, tech enthusiasts! If you're diving into the world of IoT (Internet of Things) and cloud computing, you're in for an adventure. Today, we're going to break down the ins and outs of remoteIoT SSH AWS examples. This isn't just some buzzword; it's a game-changer for how devices communicate securely over the internet. So, buckle up because we’re about to deep-dive into this topic, and by the end, you'll be equipped with the knowledge to leverage remoteIoT SSH on AWS like a pro. Now, let's get this party started!
Before we dive deep, it's important to understand what we're dealing with here. RemoteIoT SSH AWS examples are essentially blueprints that help developers set up secure communication between IoT devices and AWS servers. AWS (Amazon Web Services) is one of the most robust platforms for cloud computing, and when paired with IoT, the possibilities are endless. Whether you're managing smart home devices or industrial automation systems, understanding this setup is crucial.
Now, you might be wondering why SSH is so important in this context. Well, SSH (Secure Shell) is the backbone of secure communication over the internet. It ensures that data transmitted between your IoT devices and AWS servers remains encrypted and protected from prying eyes. This is particularly vital in today's world, where data breaches and cyber threats are on the rise. Let's move forward and explore this fascinating world in more detail.
Read also:Alex Edelman Daughter The Rising Star In Her Own Right
Understanding RemoteIoT SSH AWS: The Basics
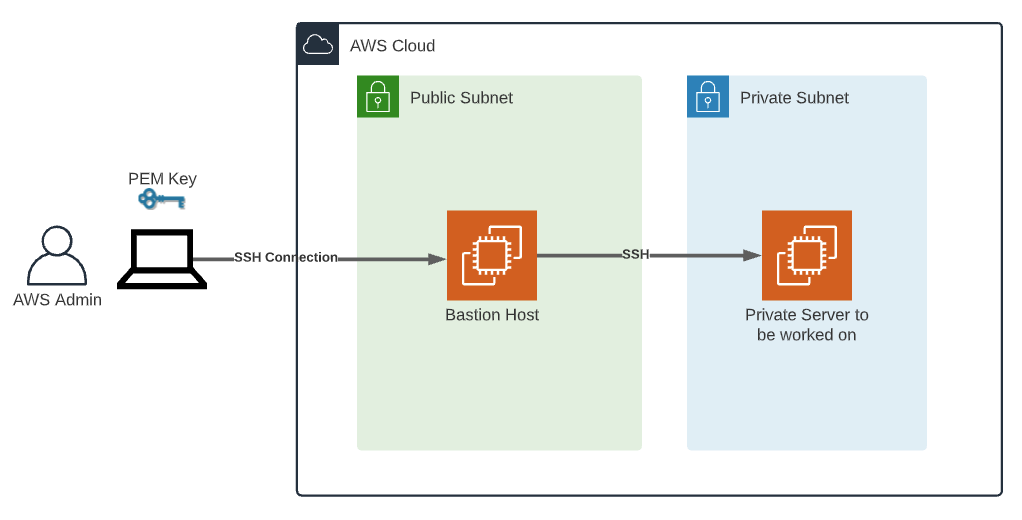
Alright, let's break it down. RemoteIoT SSH AWS is all about connecting IoT devices to AWS infrastructure using SSH protocols. This setup allows developers to manage, monitor, and control devices remotely while maintaining top-notch security. Think of it as a virtual bridge that connects your physical devices to the cloud, enabling seamless data exchange.
Why Choose AWS for IoT?
AWS offers a suite of services specifically designed for IoT, making it a go-to platform for developers. Some key features include:
- AWS IoT Core: A managed cloud service that lets connected devices interact with cloud applications and other devices securely.
- Scalability: AWS can handle millions of devices and trillions of messages, ensuring your system grows with your needs.
- Security: AWS provides end-to-end encryption and authentication, keeping your data safe from unauthorized access.
These features make AWS a powerhouse for IoT solutions, and integrating SSH only enhances its capabilities.
Setting Up RemoteIoT SSH AWS Example
Now that we have the basics down, let's talk about setting up a remoteIoT SSH AWS example. This process involves several steps, but don't worry, we'll walk you through it step by step.
Step 1: Creating an AWS Account
The first step is signing up for an AWS account. It's free to start, and AWS offers a generous free tier that's perfect for experimenting and learning. Once you're signed up, navigate to the AWS Management Console and set up your IoT environment.
Step 2: Configuring AWS IoT Core
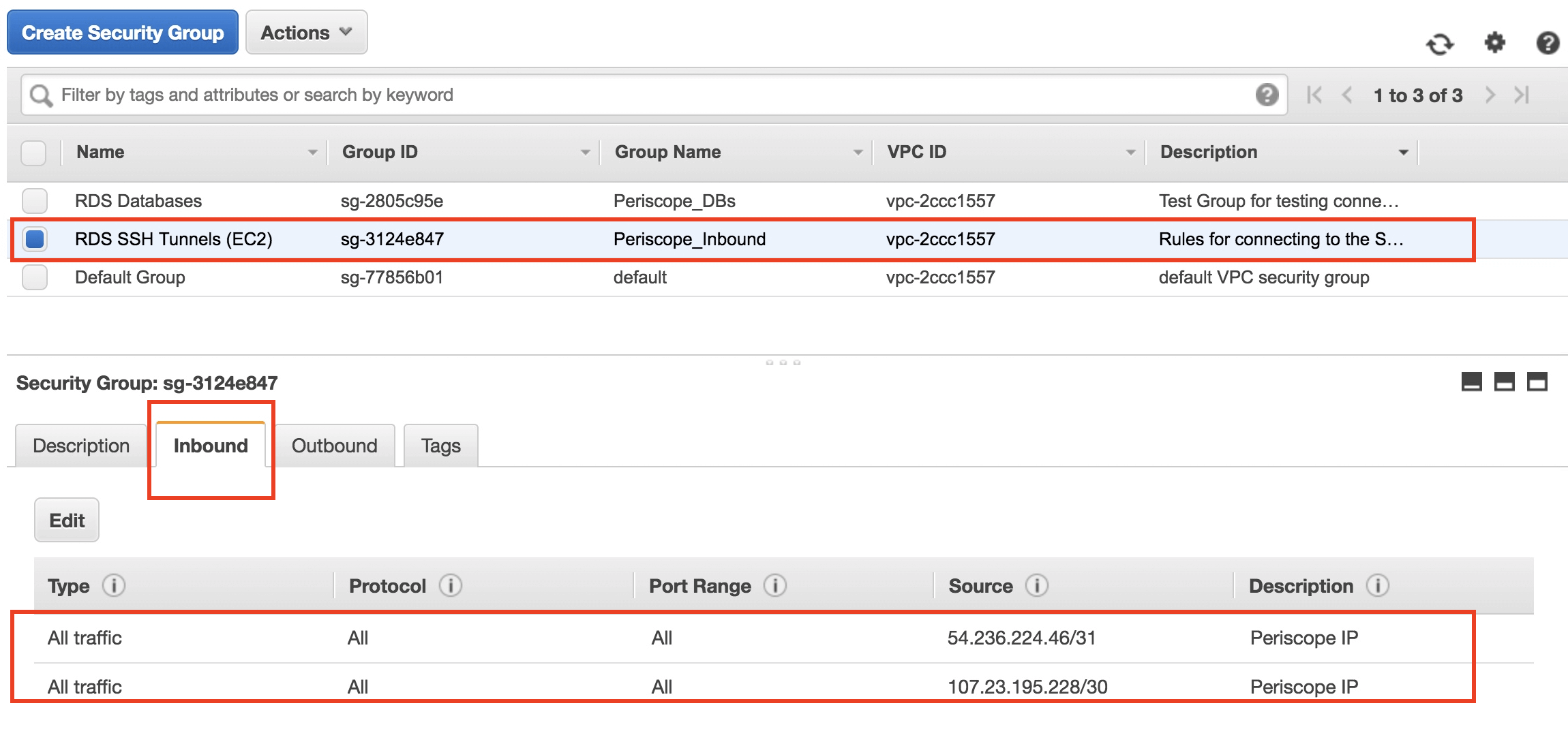
Next, configure AWS IoT Core to manage your devices. This involves setting up certificates and policies to ensure secure communication. AWS provides detailed documentation to guide you through this process.
Read also:Condom Calculator Your Ultimate Guide To Finding The Perfect Fit
Step 3: Setting Up SSH
With your AWS IoT Core configured, it's time to set up SSH. This involves generating SSH keys and configuring your IoT devices to use them. SSH ensures that all data exchanged between your devices and AWS is encrypted and secure.
Best Practices for RemoteIoT SSH AWS
Implementing remoteIoT SSH AWS requires adherence to best practices to ensure optimal performance and security. Here are some tips:
- Regular Updates: Keep your devices and software up to date to protect against vulnerabilities.
- Strong Authentication: Use strong passwords and multi-factor authentication to secure your AWS account.
- Monitoring: Regularly monitor your IoT devices and AWS environment for any suspicious activity.
By following these practices, you can ensure that your remoteIoT SSH AWS setup remains secure and efficient.
Data Security in RemoteIoT SSH AWS
Data security is a top priority when working with remoteIoT SSH AWS. AWS provides several layers of security to protect your data, including encryption, access control, and auditing. It's crucial to understand these features and implement them effectively in your setup.
Encryption in Action
Encryption is the process of converting data into a coded format that can only be read by someone with the decryption key. AWS uses industry-standard encryption protocols to secure data both in transit and at rest. This ensures that even if data is intercepted, it remains unreadable to unauthorized parties.
Real-World Applications of RemoteIoT SSH AWS
Now, let's look at some real-world applications of remoteIoT SSH AWS. From smart homes to industrial automation, the possibilities are endless.
Smart Home Automation
RemoteIoT SSH AWS can be used to manage smart home devices, such as thermostats, lighting systems, and security cameras. This allows homeowners to control their devices remotely while ensuring that their data remains secure.
Industrial Automation
In industrial settings, remoteIoT SSH AWS can be used to monitor and control machinery, optimize production processes, and reduce downtime. This leads to increased efficiency and cost savings for businesses.
Challenges and Solutions in RemoteIoT SSH AWS
While remoteIoT SSH AWS offers numerous benefits, it also comes with its own set of challenges. Some common challenges include:
- Complexity: Setting up and managing an IoT environment can be complex, especially for beginners.
- Cost: AWS services can become expensive as your system scales.
- Security Risks: As with any internet-connected system, there's always a risk of cyber attacks.
To overcome these challenges, it's important to invest in training, plan your costs carefully, and implement robust security measures.
Future Trends in RemoteIoT SSH AWS
The future of remoteIoT SSH AWS looks bright, with several trends emerging that promise to revolutionize the industry.
Edge Computing
Edge computing involves processing data closer to the source, reducing latency and improving performance. This trend is expected to play a significant role in the future of IoT and cloud computing.
Artificial Intelligence
AI is increasingly being integrated into IoT systems, enabling smarter decision-making and automation. This trend is expected to enhance the capabilities of remoteIoT SSH AWS setups.
Expert Insights and Recommendations
According to industry experts, the key to success with remoteIoT SSH AWS lies in understanding your specific needs and tailoring your setup accordingly. Whether you're a small business or a large enterprise, there's an AWS IoT solution that can meet your requirements.
Additionally, experts recommend staying informed about the latest trends and technologies in IoT and cloud computing to ensure that your system remains cutting-edge.
Conclusion
In conclusion, remoteIoT SSH AWS examples provide a powerful framework for managing IoT devices securely and efficiently. By understanding the basics, following best practices, and staying informed about the latest trends, you can unlock the full potential of this technology.
We encourage you to share your thoughts and experiences in the comments below. Whether you're a seasoned developer or just starting out, your input is valuable. And don't forget to check out our other articles for more insights into the world of IoT and cloud computing. Until next time, keep innovating and stay secure!
Table of Contents
- Understanding RemoteIoT SSH AWS: The Basics
- Why Choose AWS for IoT?
- Setting Up RemoteIoT SSH AWS Example
- Best Practices for RemoteIoT SSH AWS
- Data Security in RemoteIoT SSH AWS
- Real-World Applications of RemoteIoT SSH AWS
- Challenges and Solutions in RemoteIoT SSH AWS
- Future Trends in RemoteIoT SSH AWS
- Expert Insights and Recommendations
- Conclusion