Listen up, tech enthusiasts! If you're diving into the world of IoT and remote management, you need to get familiar with RemoteIoT platform SSH key. This isn't just some random tech jargon; it's your golden ticket to secure, seamless communication between devices. Whether you're a developer, an admin, or just someone who wants to keep their IoT systems locked down, understanding SSH keys is crucial. So, buckle up, because we're about to take you on a journey through the ins and outs of RemoteIoT platform SSH keys.
Imagine this: you're managing a network of IoT devices scattered across different locations. How do you ensure that your data stays safe and your devices remain secure? That's where SSH keys come in. They're like the digital bouncers at a club, making sure only the right people get access. RemoteIoT platform SSH key is specifically designed to handle the unique challenges of IoT environments, and we're here to break it all down for you.
Before we dive deep, let's set the stage. This article isn't just a quick overview; it's a comprehensive guide that covers everything from the basics to advanced techniques. We'll explore what SSH keys are, how they work within the RemoteIoT platform, and why they're so important for your IoT infrastructure. So, whether you're a beginner or a seasoned pro, there's something here for everyone. Let's get started!
Read also:Bollyflix Site Your Ultimate Destination For Bollywood Entertainment
What is RemoteIoT Platform SSH Key?
Alright, let's start with the basics. A RemoteIoT platform SSH key is essentially a pair of cryptographic keys used for secure communication between devices. Think of it as a digital handshake that ensures both parties are who they say they are. These keys come in two flavors: public and private. The public key is shared with the devices you want to connect to, while the private key stays safely tucked away on your system.
Why is this important? Well, in the IoT world, security is everything. With so many devices connected to the internet, the risk of unauthorized access is real. SSH keys provide an extra layer of protection, making it much harder for hackers to break in. They're like the Fort Knox of digital security, keeping your data safe and sound.
Why Use SSH Keys for IoT Devices?
Now, you might be wondering why SSH keys are such a big deal for IoT devices. Here's the deal: IoT systems are often deployed in environments where physical security isn't always a priority. This means that traditional security measures, like passwords, just don't cut it. SSH keys offer a more robust solution, providing authentication without the need for passwords.
But that's not all. SSH keys also enable encrypted communication, meaning that even if someone intercepts your data, they won't be able to make sense of it. This is particularly important for sensitive information, like financial data or personal details. Plus, with SSH keys, you can automate connections between devices, making your IoT network more efficient and easier to manage.
Benefits of Using SSH Keys in RemoteIoT Platform
- Enhanced security through public-key cryptography
- Eliminates the need for password-based authentication
- Supports automated, secure connections between devices
- Provides encrypted communication to protect sensitive data
How Does SSH Work in RemoteIoT Platform?
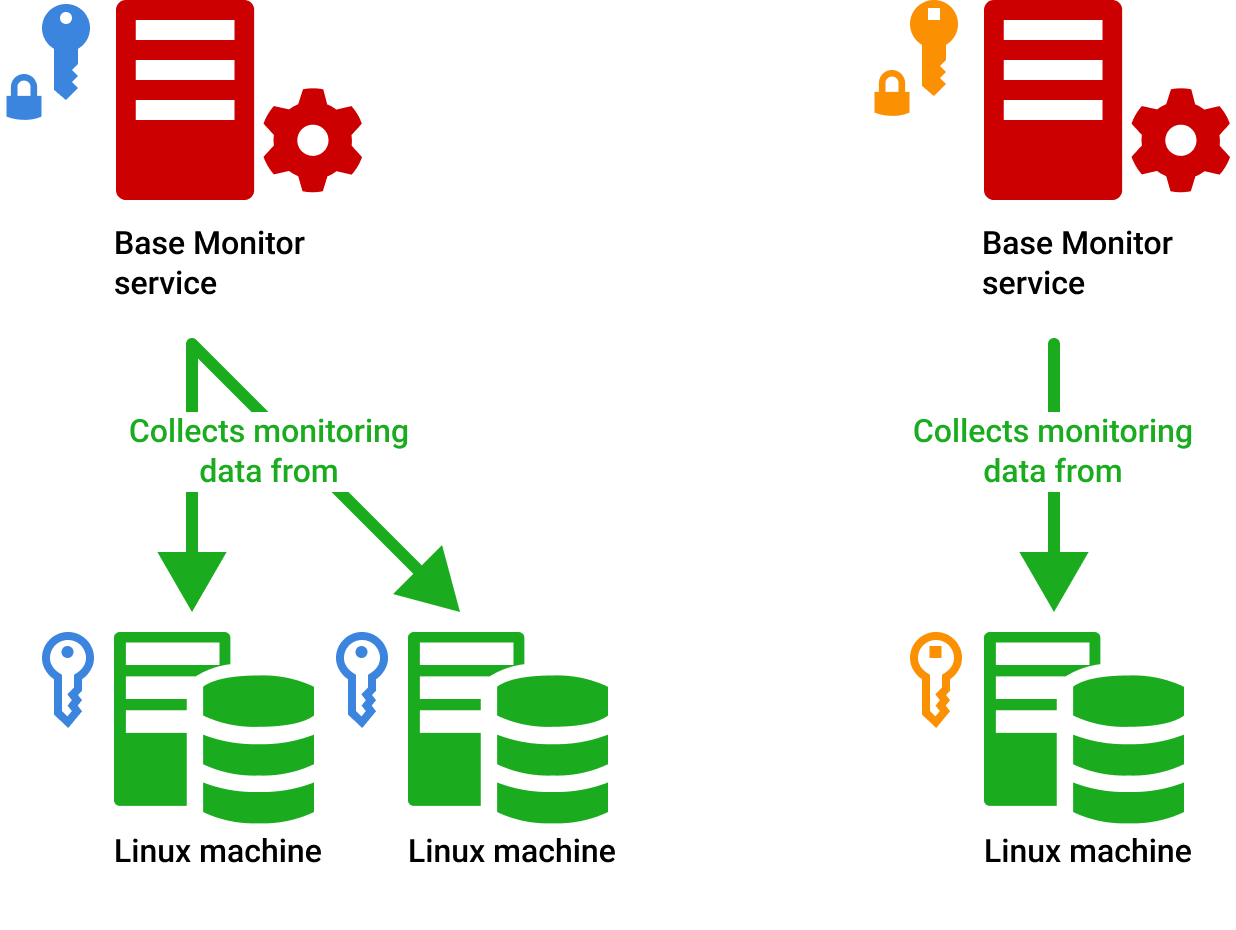
Let's break it down. When you set up an SSH key in the RemoteIoT platform, you're essentially creating a secure channel for communication. Here's how it works: first, you generate a key pair on your system. The public key is then uploaded to the RemoteIoT platform, while the private key remains on your device. When you try to connect to a device, the platform uses the public key to verify your identity. If everything checks out, you're granted access.
But wait, there's more. Once the connection is established, all communication between your device and the RemoteIoT platform is encrypted. This means that even if someone tries to eavesdrop, they won't be able to decipher the data. It's like having a private conversation in a crowded room; only you and the person you're talking to can understand what's being said.
Read also:Unveiling The Mysteries Of Waardenburg Syndrome A Deep Dive With Henning Wehn
Setting Up SSH Keys in RemoteIoT Platform
Ready to get started? Setting up SSH keys in the RemoteIoT platform is easier than you might think. Here's a step-by-step guide to help you through the process:
Step 1: Generate Your SSH Key Pair
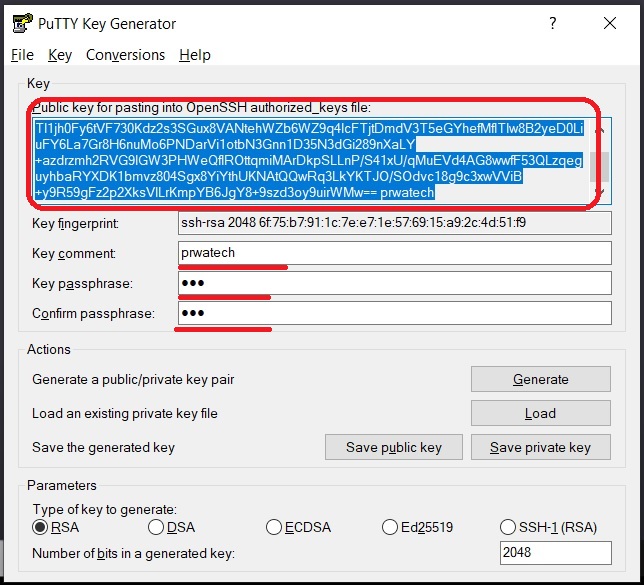
First things first, you need to generate a key pair. You can do this using a tool like ssh-keygen, which is included with most Linux and macOS systems. Just open your terminal and type:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This will create a new RSA key pair with a key size of 4096 bits. The -C option allows you to add a comment, which is usually your email address. Once the process is complete, you'll have two files: id_rsa (your private key) and id_rsa.pub (your public key).
Step 2: Upload Your Public Key
Next, you need to upload your public key to the RemoteIoT platform. This can usually be done through the platform's web interface. Just navigate to the SSH settings section and follow the instructions to upload your key. Make sure to keep your private key safe; if it falls into the wrong hands, it could compromise your security.
Step 3: Test Your Connection
Once your key is uploaded, it's time to test your connection. Open your terminal and try connecting to one of your devices using the ssh command. If everything is set up correctly, you should be able to connect without entering a password. If you run into any issues, double-check your settings and make sure your key is properly configured.
Best Practices for Managing SSH Keys
Now that you know how to set up SSH keys, let's talk about best practices. Managing SSH keys properly is crucial for maintaining the security of your IoT network. Here are a few tips to keep in mind:
- Use strong, unique keys for each device
- Regularly rotate your keys to minimize the risk of compromise
- Limit access to your private keys and store them securely
- Monitor key usage and revoke access for unused or compromised keys
Common Issues and Troubleshooting
Even the best-laid plans can go awry, and SSH keys are no exception. If you're having trouble with your RemoteIoT platform SSH key, here are a few common issues and how to fix them:
Issue 1: Permission Denied (Public Key)
This error usually means that your public key isn't properly configured on the server. Double-check that your key is uploaded correctly and that the file permissions are set properly. You might also want to verify that your private key is in the correct location on your system.
Issue 2: Connection Timeout
If you're experiencing connection timeouts, it could be due to network issues or firewall settings. Make sure that your firewall allows SSH traffic and that your network configuration is correct. You might also want to check your server logs for more information.
Security Considerations for RemoteIoT Platform SSH Keys
Security should always be at the forefront of your mind when working with SSH keys. Here are a few things to keep in mind:
First, make sure you're using strong, unique keys for each device. Avoid reusing keys across multiple systems, as this increases the risk of compromise. Additionally, consider implementing two-factor authentication (2FA) for an extra layer of security.
It's also important to regularly review your key usage and revoke access for any keys that are no longer needed. This helps minimize the attack surface and ensures that only authorized users have access to your systems.
Future Trends in IoT Security and SSH Keys
As the IoT landscape continues to evolve, so too will the security measures used to protect it. One trend to watch is the increasing use of quantum-resistant algorithms for SSH keys. These algorithms are designed to withstand attacks from quantum computers, which could potentially break traditional encryption methods.
Another trend is the integration of AI and machine learning into IoT security systems. These technologies can help detect and respond to threats in real time, providing a more proactive approach to security. As these advancements continue, SSH keys will remain a critical component of IoT security, ensuring that devices can communicate securely and efficiently.
Conclusion
So there you have it, folks! RemoteIoT platform SSH keys are a vital tool for securing your IoT infrastructure. From enhancing security to automating connections, they offer a wide range of benefits that make them indispensable for anyone working in the IoT space.
Now that you've got the scoop, it's time to take action. Set up your SSH keys, follow best practices, and stay ahead of the curve when it comes to IoT security. And don't forget to share this article with your friends and colleagues; the more people know about SSH keys, the safer our digital world will be.
Table of Contents
- What is RemoteIoT Platform SSH Key?
- Why Use SSH Keys for IoT Devices?
- How Does SSH Work in RemoteIoT Platform?
- Setting Up SSH Keys in RemoteIoT Platform
- Best Practices for Managing SSH Keys
- Common Issues and Troubleshooting
- Security Considerations for RemoteIoT Platform SSH Keys
- Future Trends in IoT Security and SSH Keys
- Conclusion