Ever wondered how to access your RemoteIoT devices securely when they're tucked away behind a firewall? Well, buckle up because we're diving deep into this tech mystery today. Imagine you’ve got all these smart gadgets humming along nicely in your home or office, but you want to control them from afar—like, really far. That’s where RemoteIoT comes in, but here's the twist: you need to do it safely, behind a firewall, and with a Mac server as your trusty sidekick. Sounds tricky? Not anymore.
This guide isn’t just another tech mumbo-jumbo post. We’re breaking down the process step by step so you can set everything up like a pro. Whether you're a tech enthusiast, a small business owner, or someone who just loves tinkering with IoT devices, this article is for you. No fancy jargon, just plain talk that gets the job done.
Before we jump into the nitty-gritty, let me reassure you—this isn’t rocket science. Sure, it involves some networking basics and server setup, but trust me, if I can do it, so can you. And hey, who doesn’t love a good challenge? So grab your favorite beverage, sit back, and let’s unravel the secrets of using RemoteIoT behind a firewall with a Mac server example.
Read also:Cheri Oteri Partner The Untold Story Behind The Comedy Queens Love Life
Understanding RemoteIoT and Firewalls
First things first, let’s clarify what we’re dealing with. RemoteIoT refers to any system or setup that allows you to manage Internet of Things (IoT) devices remotely. Think of it as the remote control for your smart home, but way cooler and more powerful. Now, firewalls are like the bouncers at a club—they decide who gets in and who stays out. In this case, your firewall is protecting your network from unwanted visitors while letting the good stuff through.
Why does this matter? Well, if you want to access your RemoteIoT devices from outside your local network, you’ll need to convince your firewall to let you in. This is where the magic happens, and your Mac server becomes the key to unlocking this puzzle.
Let’s break it down further. A Mac server can act as a gateway, allowing secure access to your IoT devices without compromising your network’s safety. By setting up port forwarding, SSH tunnels, or even using a reverse proxy, you can create a secure pathway through your firewall. It’s like building a secret tunnel that only you know about.
Why Use a Mac Server?
You might be wondering why we’re focusing on Mac servers. Here’s the deal: Macs come equipped with powerful tools like macOS Server, which makes setting up secure connections a breeze. Plus, they’re built on Unix, which means they’re naturally good at handling network configurations and security protocols.
Using a Mac server for RemoteIoT behind a firewall offers several advantages:
- Security: Mac servers are less prone to attacks compared to other platforms, making them ideal for handling sensitive data.
- Ease of Use: The intuitive interface and pre-installed tools simplify the setup process, even for beginners.
- Compatibility: Mac servers work seamlessly with most IoT devices, ensuring smooth communication across your network.
- Scalability: Whether you’re managing a few devices or an entire fleet, a Mac server can grow with your needs.
Plus, let’s face it—Apple products just have that cool factor. Who wouldn’t want to say they’ve got a Mac server powering their IoT empire?
Read also:Kat Timpf New Baby Name The Cutest Addition To The Family
Setting Up Your Mac Server
Alright, let’s get our hands dirty. The first step in using RemoteIoT behind a firewall is setting up your Mac server. Don’t worry; it’s not as complicated as it sounds. Here’s a quick rundown:
1. Install macOS Server: Head over to the Mac App Store and download macOS Server. It’s free and will give you access to all the server management tools you’ll need.
2. Create a Server: Once installed, open the Server app and follow the on-screen instructions to create a new server. You’ll be prompted to choose services like File Sharing, Websites, or VPN. For our purposes, focus on enabling Remote Management and SSH.
3. Set Up User Accounts: Create a dedicated user account for managing your IoT devices. This ensures that only authorized users can access your network.
4. Configure Security Settings: Enable encryption and set up strong passwords to protect your server from unauthorized access.
With your Mac server up and running, you’re ready to tackle the next step: configuring your firewall.
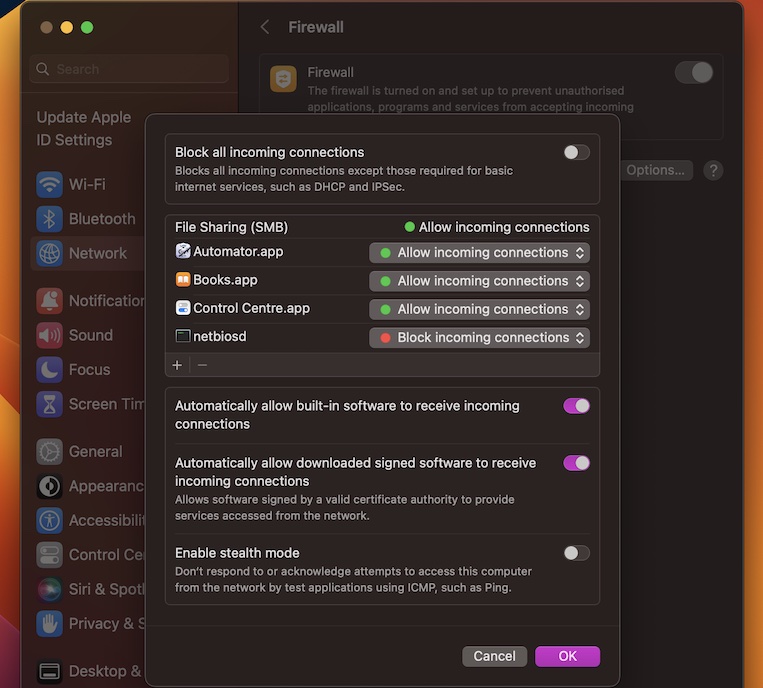
Configuring Your Firewall for RemoteIoT
Now that your server is ready, it’s time to configure your firewall. This is where the real action happens. The goal is to allow your Mac server to communicate with your IoT devices while keeping everything secure.
Here’s how you can do it:
1. Identify Open Ports: Check which ports your IoT devices are using. Common ones include 80 (HTTP), 443 (HTTPS), and 22 (SSH).
2. Set Up Port Forwarding: Log in to your router’s admin panel and set up port forwarding rules. Forward the necessary ports to your Mac server’s IP address.
3. Enable SSH Tunneling: SSH tunnels provide a secure way to access your network remotely. Configure your Mac server to accept SSH connections and use a client like PuTTY or Terminal to establish the tunnel.
4. Test the Connection: Use tools like ping or telnet to verify that your firewall rules are working correctly. If everything’s set up right, you should be able to access your IoT devices without any issues.
Remember, security is key here. Always use strong passwords, enable two-factor authentication, and keep your software updated to protect against potential threats.
Common Firewall Issues and Solutions
As you configure your firewall, you might run into a few hiccups. Here are some common issues and how to fix them:
- Connection Refused: Double-check your port forwarding rules and ensure that your server is listening on the correct ports.
- Timeout Errors: Make sure your firewall isn’t blocking incoming connections. You might need to adjust your router’s NAT settings.
- Security Alerts: If your firewall keeps flagging connections as suspicious, review your rules and whitelist your Mac server’s IP address.
Don’t get discouraged if things don’t work right away. Troubleshooting is part of the process, and with a little persistence, you’ll have everything up and running in no time.
Using SSH Tunnels for Secure Access
SSH tunnels are one of the best ways to access your RemoteIoT devices behind a firewall. They encrypt your data and provide a secure pathway between your Mac server and your IoT devices.
Here’s how you can set up an SSH tunnel:
1. Install an SSH Client: If you’re on a Mac, you already have Terminal. For Windows users, download PuTTY or a similar client.
2. Connect to Your Server: Use the command `ssh username@server_ip` to connect to your Mac server. Replace `username` and `server_ip` with your actual credentials.
3. Create the Tunnel: Use the `-L` option to forward local ports to your server. For example, `ssh -L 8080:localhost:80 username@server_ip` will forward port 8080 on your local machine to port 80 on your server.
4. Access Your Devices: Once the tunnel is established, you can access your IoT devices through your local browser or client software.
SSH tunnels are a powerful tool, but they require a bit of setup. If you’re new to this, don’t hesitate to experiment and learn as you go.
Tips for Managing SSH Tunnels
Here are a few tips to help you manage SSH tunnels effectively:
- Use Key-Based Authentication: This eliminates the need for passwords and makes your connections more secure.
- Automate Connections: Use scripts or tools like AutoSSH to automate your tunnel setups.
- Monitor Activity: Keep an eye on your server logs to detect any suspicious activity.
By following these tips, you can ensure that your SSH tunnels remain secure and reliable.
Implementing Reverse Proxy
Another method for accessing RemoteIoT devices behind a firewall is using a reverse proxy. This setup allows you to route external requests to your internal network without exposing your devices directly.
Here’s how it works:
1. Install a Web Server: Use software like Apache or Nginx to set up a reverse proxy on your Mac server.
2. Configure Proxy Rules: Set up rules to forward requests to your IoT devices. For example, you might configure `/device1` to point to `http://localhost:8080`.
3. Secure Your Proxy: Enable SSL certificates and authentication to protect your proxy from unauthorized access.
4. Test Your Setup: Use tools like curl or Postman to test your proxy and ensure it’s working as expected.
Reverse proxies offer a flexible solution for managing multiple IoT devices and can simplify your network architecture.
Benefits of Using a Reverse Proxy
Implementing a reverse proxy comes with several advantages:
- Centralized Management: Control all your IoT devices from a single point.
- Improved Security: Hide your internal network structure from outsiders.
- Scalability: Easily add or remove devices without changing your firewall rules.
While reverse proxies require some initial setup, they’re well worth the effort for anyone serious about managing RemoteIoT devices.
Troubleshooting Common Issues
Even with the best-laid plans, things can go wrong. Here are some common issues you might encounter and how to fix them:
1. Unable to Connect: Verify your server’s IP address and ensure that your firewall rules are correctly configured.
2. Slow Performance: Check your network bandwidth and optimize your server settings for better performance.
3. Authentication Errors: Double-check your usernames, passwords, and key files to ensure they’re correct.
4. Device Unreachable: Ensure that your IoT devices are properly connected to your network and that their IP addresses are static.
If you’re still stuck, don’t hesitate to consult online forums or reach out to your network administrator for help.
Staying Updated with Best Practices
Technology is always evolving, so it’s important to stay updated with the latest best practices. Follow blogs, attend webinars, and join online communities to keep your skills sharp.
Some resources to check out include:
- Apple Developer Forums: A great place to learn about macOS Server updates and features.
- IoT Security Blogs: Stay informed about the latest security trends and threats.
- Networking Communities: Connect with other professionals to exchange tips and tricks.
By staying informed, you can ensure that your RemoteIoT setup remains secure and efficient.
Conclusion and Call to Action
And there you have it—a comprehensive guide on how to use RemoteIoT behind a firewall using a Mac server example. From setting up your server to configuring your firewall and implementing advanced techniques like SSH tunnels and reverse proxies, we’ve covered everything you need to know.
Remember, the key to success lies in preparation and practice. Don’t be afraid to experiment and learn from your mistakes. And most importantly, always prioritize security to protect your network and data.
Now it’s your turn. Have you tried setting up RemoteIoT behind a firewall? What challenges did you face, and how did you overcome them? Share your experiences in the comments below and help others in the community. Don’t forget to bookmark this page for future reference and check out our other articles for more tech tips and tricks. Happy tinkering!
Table of Contents
- Understanding RemoteIoT and Firewalls
- Why Use a Mac Server?
- Setting Up Your Mac Server
- Configuring Your Firewall